How Managed Data Protection Can Safeguard Your Company’s Critical Data
How Managed Data Protection Can Safeguard Your Company’s Critical Data
Blog Article
Protect Your Data With Reputable Managed Data Security Solutions
In an era where data violations are increasingly widespread, the importance of durable information protection can not be overemphasized. Trustworthy managed data defense services, consisting of Backup as a Solution (BaaS) and Calamity Healing as a Solution (DRaaS), provide a strategic method to guarding delicate details.
Significance of Information Defense
In today's digital landscape, the relevance of data security can not be overemphasized; studies suggest that over 60% of local business that experience an information breach close within six months (Managed Data Protection). This disconcerting figure highlights the critical requirement for durable information protection approaches, particularly for organizations that handle delicate details
Data works as a crucial property for businesses, driving decision-making, client interaction, and functional performance. A data breach can not only lead to substantial economic losses but also damage an organization's credibility and wear down client depend on. Guarding information have to be a top priority for organizations of all dimensions.
In addition, governing compliance has actually become increasingly strict, with laws such as the General Data Protection Policy (GDPR) and the California Consumer Personal Privacy Act (CCPA) enforcing hefty charges for non-compliance. Organizations should implement detailed data defense gauges to minimize lawful dangers and copyright their obligation to safeguard customer details.
Kinds Of Managed Solutions
The landscape of information security solutions has actually developed to fulfill the growing needs for protection and compliance. Taken care of options can be categorized right into a number of kinds, each tailored to resolve certain business requirements.
One common kind is Back-up as a Service (BaaS), which automates the back-up procedure and guarantees information is firmly stored offsite. This technique reduces the risk of information loss due to hardware failings or disasters.
Catastrophe Recuperation as a Service (DRaaS) is one more crucial option, supplying organizations with the capacity to recover and restore their whole IT framework quickly after a disruptive occasion. This guarantees service connection and reduces the influence of downtime.
Additionally, Cloud Storage options supply flexible and scalable data storage space alternatives, allowing companies to handle and access their information from anywhere, hence improving cooperation and productivity.
Managed Protection Services (MSS) likewise play an important duty, integrating various safety actions such as hazard discovery and reaction, to safeguard sensitive information from cyber dangers.

Key Attributes to Search For
Selecting the appropriate managed information defense remedy requires mindful consideration of crucial features that line up with a company's certain requirements. Scalability is essential; the remedy should fit expanding information volumes without jeopardizing performance. Additionally, try to find extensive protection that consists of not only backup and recuperation yet also data archiving, making certain all crucial information is protected.
Another crucial attribute is automation. A solution that automates backup procedures lowers the threat of human mistake and ensures image source consistent data defense. Moreover, robust security steps, such as file encryption both en route and at remainder, are critical to safeguard sensitive information from unauthorized access.
In addition, the company must supply adaptable healing choices, consisting of granular healing for private files and full system recovers, to lessen downtime throughout data loss events. Surveillance and reporting capacities likewise play a substantial duty, as they enable organizations to track the status of back-ups and get notifies for any concerns.
Last but not least, think about the supplier's online reputation and support services - Managed Data Protection. Reliable technological support and a proven record in the market can substantially influence the performance of the handled data defense option
Benefits of Selecting Managed Solutions
Why should organizations consider managed data defense services? The key benefit lies in the specialized experience that these solutions offer. By leveraging a group of experts dedicated to information protection, companies can guarantee that their information is protected versus developing threats. This know-how translates right into even more durable safety actions and compliance with sector regulations, minimizing the danger of data violations.
One more substantial benefit is set you back efficiency. Handled solutions often decrease the requirement for hefty ahead of time investments in hardware see and software application, permitting companies to allocate sources much more successfully. Organizations just spend for the solutions they make use of, which can result in substantial savings with time.
Additionally, handled solutions supply scalability, making it possible for companies to readjust their information defense approaches in line with their growth or altering company requirements. This flexibility guarantees that their data protection steps remain effective as their functional landscape advances.
Steps to Execute Solutions
Executing managed information defense options includes a series of strategic actions that make certain effectiveness and positioning with organizational objectives. The primary step is conducting a complete evaluation of your current data landscape. This includes determining essential information assets, evaluating existing protection measures, and identifying susceptabilities.
Next, specify clear goals based on the analysis results. Determine what information have to be shielded, needed recuperation time goals (RTO), and recovery factor goals (RPO) This quality will certainly guide remedy selection.
Following this, involve with managed provider (MSPs) to explore Read Full Report prospective solutions. Review their know-how, solution offerings, and compliance with sector standards. Partnership with stakeholders is essential throughout this stage to guarantee the picked solution satisfies all functional requirements.
As soon as an option is picked, develop a detailed implementation plan. This strategy ought to detail source allocation, timelines, and training for personnel on the brand-new systems.
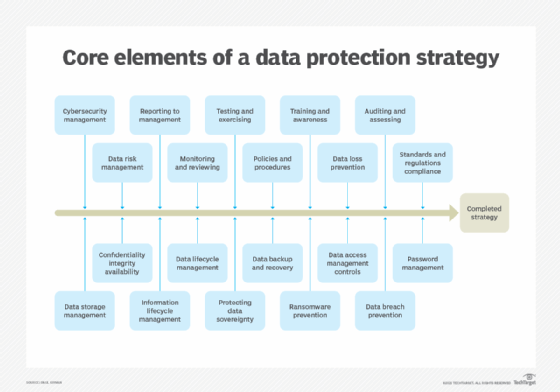
Conclusion
In conclusion, the implementation of reliable taken care of data protection options is essential for safeguarding delicate info in a significantly electronic landscape. By leveraging services such as Back-up as a Solution (BaaS) and Catastrophe Recovery as a Solution (DRaaS), companies can boost their information safety through automation, scalability, and durable file encryption. These steps not just ensure compliance with regulatory requirements however also foster depend on among stakeholders and consumers, eventually contributing to service durability and continuity.
In an era where information breaches are significantly prevalent, the relevance of robust data protection can not be overemphasized. Reputable managed information defense options, consisting of Backup as a Solution (BaaS) and Disaster Recovery as a Service (DRaaS), offer a calculated technique to safeguarding delicate details.Choosing the appropriate managed information protection option requires careful factor to consider of key features that straighten with a company's particular needs. Additionally, look for extensive insurance coverage that includes not just backup and healing yet additionally data archiving, guaranteeing all important information is secured.
By leveraging a team of experts committed to information protection, organizations can make sure that their information is secured against advancing threats.
Report this page